RIIM Technology Overview
Radiocrafts has developed an IP based wireless mesh solution to enable end-to-end IP communication between IoT devices and the Cloud. We call this solution RIIM, Radiocrafts Industrial IP Mesh. The use of end-to-end IP is
a trend in order to reuse the networks, protocols and solutions from the normal internet in the IoT business.
The benefits are that an IP- mesh solution removes the need for complex gateway solutions and allows all end points to be accessed directly from the Cloud without a proprietary addressing solution.

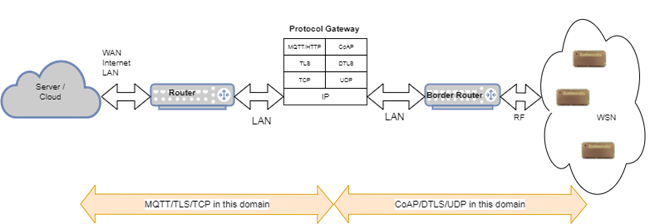
CoAP Application Protocol
Constrained Application Protocol (CoAP) is a specialized web transfer protocol for use with constrained nodes and constrained networks in the Internet of Things. CoAP is designed to enable simple, constrained devices to join the IoT even through constrained networks with low bandwidth and low availability. It is generally used for machine-to-machine (M2M) applications such as smart energy and building automation. The protocol was designed by the Internet Engineering Task Force (IETF), CoAP is specified in IETF RFC 7252.
RIIM supports CoAP but there are also possibilities to do application gateways somewhere in the connection and this is shown in Figure 3. The concept is basically that the transport and application layer can be converted from UDP/DTLS/COAP to TCP/TLS/MQTT (HTTP). Such a solution is more complex and challenging to setup, but it gives the advantage that the two protocol suites can be optimize for different network properties. A protocol gateway can be implemented very easily on any standard linux computer using open source conversion tools.
Scalability
One of the principle challenges in IoT is the huge number of devices and the addressability of them. This is part of the reason that the number of available IPv4 addresses for new products are going toward zero and that the
IETF introduced IPv6. IPv6 increases the number of available addresses significantly, which will ensure that every IoT device can get its own IP address which can be valid globally.
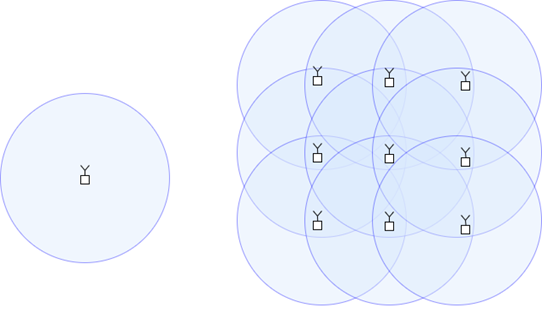
Coverage/Mesh
LPWAN is commonly used term for long range IoT networks. There are several ways to get larger coverage.
- Use higher output power (Normally limited by regulation)
- Better sensitivity. (No leaps in technology, so only way to achieve this is by reducing data rate.
- Multi-hop/mesh solution. (Requires router)
The basic advantage of mesh is greater coverage. Any router device can forward data from one node to the next and communication between devices normally out of radio range is possible. By using a mesh, the end devices/sleeping node can continue to send short/energy efficient packets and thus have long battery lifetime, while still be spread over a wider area.
The mesh topology used in RIIM enable completely self-configuring and self-healing networks. This means that no network management is needed. An intelligence is included in each node to find the optimized route to the border router to ensure the most reliable connection.
The max number of nodes in the mesh is not a fixed number. It will be affected by the topology, data packet sizes, data traffic, security setting etc. RIIM utilize source routing down into the network. This limit the memory requirement on each routing mesh device, and require more memory on the border router. The border router in RIIM contains >4 times the amount of RAM compared to the child nodes and thus allow several hundred nodes given that the data traffic to each is limited.
But all large network should be verified with the actual data traffic pattern and topology intended.
Reliable, Low Power and Low Latency Through 6TiSCH
As part of the IP development for low power low data rate network, 6TiSCH has also been developed. It defines how IPv6 can be used together with TSCH (Time Slotted Frequency Hopping). TSCH was introduced in IEEE 802.15.4:2012 and is a combination of Time division multiple access and Frequency-division multiple access. This means that transmissions are done at several frequencies and at different time slots in a synchronized schedule.
TSCH give very high reliability, low predictable latency and low power. The use of multiple frequencies gives robustness against jamming, noise, collisions and multipath problems. As the time slots are well defined, the latency of a packet from one node to another is deterministic. The use of timeslots also gives the nodes a defined time to go to sleep and thereby conserve power in an efficient way.
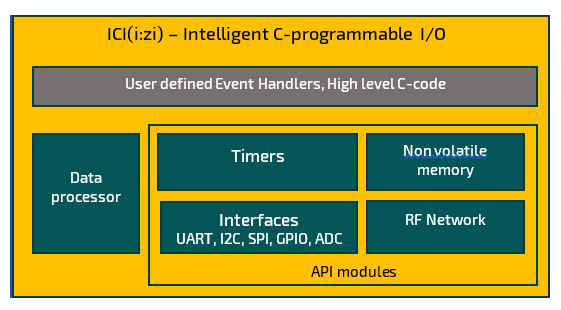
ICI (i:zi), Application Development in no Time.
One of the unique features of the RIIM suite is the ease of development. As chips, stacks and solutions are becoming more and more feature rich, the complexity also increases. 10 years ago a typical sensor application was written as bare metal code based on super loop/while(1) loop in 8-16 kB of code.
Today’s solutions are often based on an OS, a complex stack and high-level security giving a total of 100kB+. When solutions are becoming more complex, they easily require longer development cycles with higher risk.
To combat this, Radiocrafts introduces the ICI (i:zi) concept for intelligent C-programmable sensor and actuator interfaces and control at the end nodes. The core of ICI (i:zi) is to abstract all the complexity of the solution and give the user an easy and intuitive API to write his code.
Example: The user has his specific requirement like:
- When I press a button device shall try to join
- When joining successful blink green led.
- Read an I2C sensor every 15 seconds.
- If above a certain level send alarm via RF
- Send last read sensor value every 5 minutes (even without alarm)
- Allow the Cloud application to send message in changing the sensor_ interval and threshold
The ICI (i:zi) concept allows the user to write his six different event handlers from above example without any knowledge of the architecture of the hardware and avoid spending time interfacing to the wireless stack, threads in the RTOS system and inter-thread communication and other complex issues.
Visit Radiocrafts’ GitHub page to explore sample codes for RIIM applications and features.
OTA Firmware Update
A very important feature for future proofing the network is the Over the Air (OTA) capabilities. The pace of innovation and change in the IoT business is rapid and imagining a firmware being fixed without modifications for 10 years seem unlikely. Due to this capability to upgrade the firmware from a central point is a key capability.
For OTA the RIIM has implemented an OAD function based on CoAP packets Over UPD. This is the same concept chosen for OAD in LWM2M-standard from the Open Mobile Alliance.
The new firmware image received via RF is stored in a flash memory and is normally encrypted. The image is decrypted, verified and authenticated before loaded into active memory in order to protect against malware or hacking.
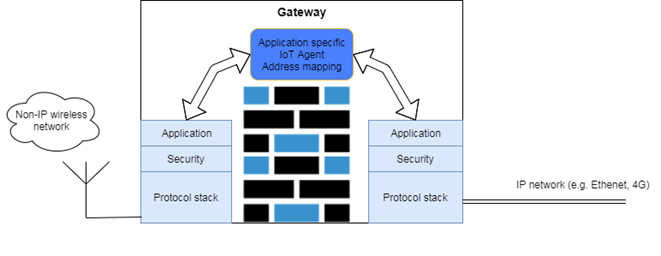
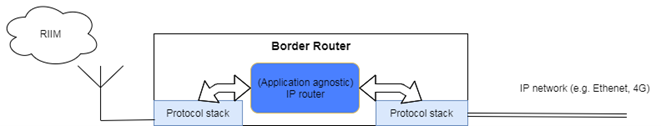
Border Router (Gateway) Solution
In normal legacy M2M, the gateway needs to implement the IoT agent. This means that the gateway is the end point for the internet connection. Basically, the gateway becomes a broker between the IP based traffic on one side and the wireless network on the other. Any incoming packet from one network must be decoded and analyzed and the mapping function to what packet to send out on the other network must be done.
The IoT agent in the gateway becomes quite complex and need to include address mapping, mapping packet types in one protocol to packet type on the other protocol. It must map the application packet and it must map the IP addresses to a local address.
With IP mesh, there is no need for a Gateway. The end point contains the IoT agent and the work of the border router is simply to route the IP packets from wireless network to the WAN. Due to this the box connecting a wireless IP mesh network to the wired internet are normally referred to as border router or edge router.
All addressing, encryption and application messages goes end-to-end, and this enhance security and reduce complexity.
Since the border router is a generic device that can be reused in many different applications, Radiocrafts have developed our own border router device that can be utilized directly as a product without further development cost.
Security (DTLS/TLS)
When using IP based networks all security mechanism can be utilized end to end. That means protocols like DTLS/TLS can be used between end nodes and endpoint in the cloud service. This way the gateway does not know the encryption keys used, and any hacking of the gateway will not threaten the confidentially of data end to end.
This present a huge advantage toward existing solution with proxy gateway. There the gateway itself have the data unsecure and the gateway itself becomes a security vulnerability.
TLS/DTLS is the state of the art security mechanism used in the internet and gives future proof system and known protocols for the cloud developer compared to using proprietary security protocols that might be outdated, buggy and unknown to network operator.
